How To Setup a VPN Kill Switch Server
This will show you how to set up a VPN Kill Switch so all traffic will come from that server. For this server, I am using CentOS, but you can easily use Ubuntu server if you are more familiar with that.
Install packages
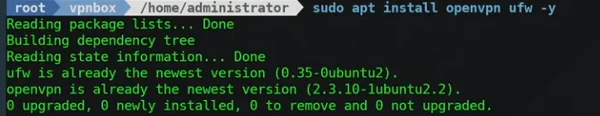
sudo apt install openvpn ufw -y
*Note: use apt instead of dnf on Ubuntu or Debian Servers
Set Static IP
sudo nmtuisudo nmcli connection down eth0 && sudo nmcli connection up eth0
Download OVPN Files
My recommendation for a Public VPN Provider is Express VPN. It is what I use below and in my VPN videos due to its speed and amount of servers. This is my affiliate link where you will receive an extra 3 months free for signing up for a year. https://christitus.com/expressvpn
However, you can use these instructions on ANY VPN that provides ovpn files which any reputable VPN provider has.
mv ~/Downloads/client.ovpn /etc/openvpn/test.conf
Service creation
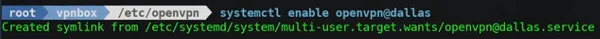
ls /lib/systemd/system/
*Check for openvpn-client@ or openvpn@sudo systemctl start openvpn@test
Disable ipv6 and Secure System
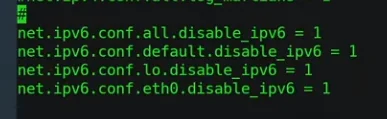
sudo nano /etc/sysctl.conf
net.ipv6.conf.all.disable_ipv6=1
net.ipv6.conf.default.disable_ipv6=1
net.ipv6.conf.lo.disable_ipv6=1
sudo sysctl -p
Verify Ipv6 is disabledcat /proc/sys/net/ipv6/conf/all/disable_ipv6sudo sysctl --all | grep disable_ipv6
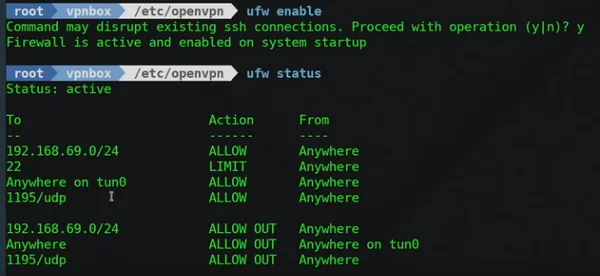
Firewall ufw blocks – VPN Kill Switch
sudo nano /etc/default/ufw
IPV6=no
Whitelist Local Area Networksudo ufw allow in to 192.168.1.0/24sudo ufw allow out to 192.168.1.0/24
Block All Incoming and Outgoing Traffic by Defaultsudo ufw default deny outgoingsudo ufw default deny incoming
Whitelist VPN Port for VPN Establishmentsudo ufw allow out to any port 1194 proto udp
*check port by doing head /etc/openvpn/expressvpn.conf
Whitelist VPN Tunnelsudo ufw allow out on tun0 from any to anysudo ufw allow in on tun0 from any to any
Enable Firewallsudo ufw enable
External Program Setup on Server
X11 Forwarding
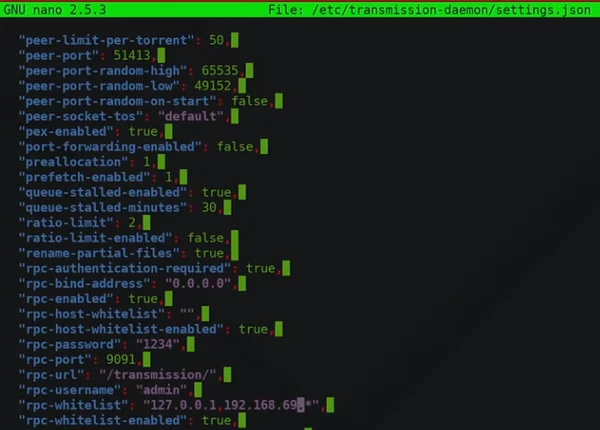
Transmission daemonsudo apt install transmission-daemonsudo systemctl stop transmission-daemonsudo nano /etc/transmission-daemon/settings.json
*enable rpc and whitelist, add blocklistsudo systemctl start transmission-daemon